Introduction to Quantum Networking
Quantum networking represents a significant advancement in the field of telecommunications, harnessing the principles of quantum mechanics to facilitate innovative forms of data transmission. Unlike classical networking, which relies on electronic signals and traditional encoding methods, quantum networking employs quantum bits, or qubits, to convey information. This fundamental shift allows for the development of networks that can potentially exceed the capacity and security limitations of conventional systems.
At its core, quantum networking utilizes phenomena such as superposition and entanglement. Superposition enables qubits to exist in multiple states simultaneously, allowing for more complex data processing than binary systems can offer. Entanglement, on the other hand, allows qubits to be interconnected in such a way that the state of one qubit can instantaneously affect the state of another, regardless of the distance separating them. This unique property has profound implications for communication speed and efficiency, potentially allowing for instantaneous information transfer across vast distances.
The security advantages of quantum networking are particularly noteworthy. Traditional networks are vulnerable to a variety of hacking methods, which exploit the inherent weaknesses in classical encryption techniques. In contrast, quantum networking employs quantum key distribution (QKD), a method that uses the principles of quantum mechanics to ensure secure communication. Any attempt to intercept or eavesdrop on the quantum signal will inherently alter its state, thereby alerting the sender and receiver to the presence of an unauthorized party. This level of security is unprecedented and represents a major leap forward in protecting sensitive data.
In exploring the potential of quantum networking, it is clear that its application could lead to revolutionary improvements in how we transmit and secure data. By fundamentally shifting the paradigms of communication and security, quantum networking stands to redefine our digital landscape for years to come.
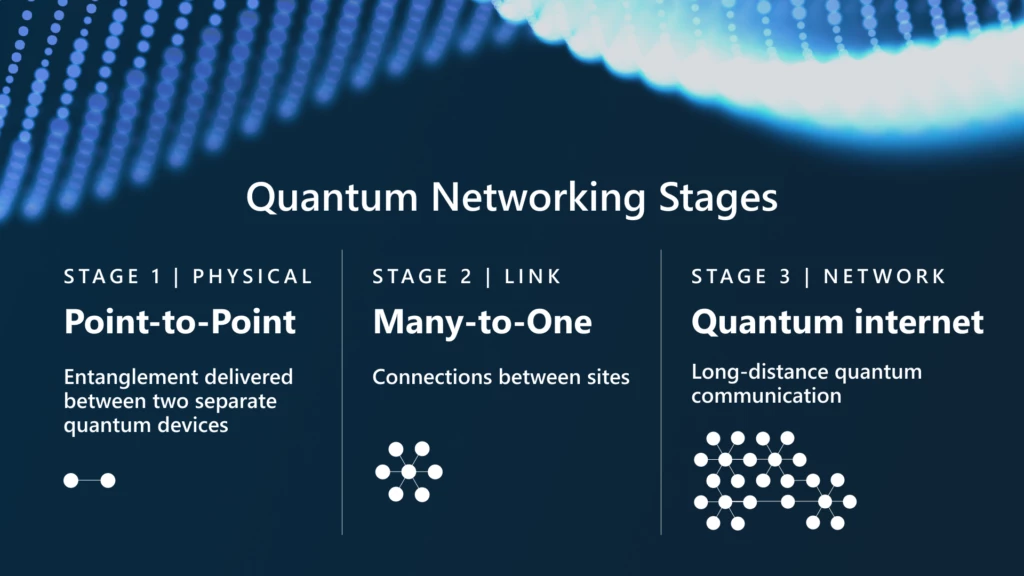
The Basics of Quantum Mechanics
Quantum mechanics serves as the fundamental basis for numerous technologies, including quantum networking. At its core, quantum mechanics explores the behavior of matter and energy at the atomic and subatomic levels. Its principles diverge significantly from classical physics, bringing forth concepts that don’t conform to traditional logical reasoning. Three prominent ideas within quantum mechanics—superposition, entanglement, and quantum bits (qubits)—are essential for understanding how quantum networking operates.
Superposition is a cornerstone of quantum theory, describing a system’s ability to exist in multiple states simultaneously until measured. This property leads to the notion that a quantum bit, or qubit, can represent both a zero and a one at the same time, unlike classical bits that are strictly binary. This characteristic allows quantum networks to process vast amounts of information more efficiently than classical systems, exponentially increasing data transfer capacity.
Another critical element is entanglement, a phenomenon where two or more particles become interconnected in such a way that the state of one particle instantaneously influences the state of another, regardless of the distance separating them. This peculiar relationship is key to quantum communication, facilitating the secure transfer of information. When entangled qubits are part of a quantum network, they can exchange data in a manner that is inherently protected from eavesdropping, making quantum networks markedly more secure than their classical counterparts.
Lastly, the concept of quantum bits or qubits is instrumental in implementing quantum networking. Qubits serve as the building blocks of quantum information processing. Utilizing the principles of superposition and entanglement, qubits enhance computational capabilities by existing in multiple states, drastically improving the efficiency and security of data transmission. Understanding these fundamental aspects of quantum mechanics lays the groundwork for exploring the intricate workings and advantages of quantum networking in the face of traditional hacking methods.
How Quantum Networking Works
Quantum networking is an advanced field that harnesses the principles of quantum mechanics to facilitate secure communication channels. At its core, this innovative technology relies on several key components, namely quantum channels, quantum repeaters, and quantum key distribution (QKD). Together, these elements create a framework for a secure network that significantly enhances data protection and integrity.
Quantum channels are the foundational pathways through which quantum information is transmitted. Unlike classical channels that encode bits as either 0s or 1s, quantum channels leverage quantum bits or qubits, which can exist in multiple states simultaneously, thanks to the principles of superposition and entanglement. This unique property empowers quantum networks to transmit information in a way that is fundamentally different and more secure than traditional methods.
Quantum repeaters play a crucial role in extending the range of quantum networks. Due to the fragility of quantum states, signals can be easily diminished over long distances. Quantum repeaters work by utilizing entanglement swapping and purification techniques, allowing the transmission of quantum information across greater distances without significant loss. This facilitates reliable communication between distant nodes in a quantum network, making it scalable and practical for wider applications.
Another vital component of quantum networking is quantum key distribution (QKD), which ensures that the keys used in encryption are shared securely. QKD utilizes the principles of quantum mechanics to detect any eavesdropping attempts. Any intrusion into the quantum state of the keys alters the state itself, alerting the communicating parties to potential security breaches. This innovative method of distributing encryption keys represents a significant advancement in data protection, as it provides a level of security unattainable by classical methods.
In conclusion, the interplay of quantum channels, quantum repeaters, and QKD forms the backbone of quantum networking, enabling a secure and robust system for data transmission that is resistant to hacking and unauthorized access.
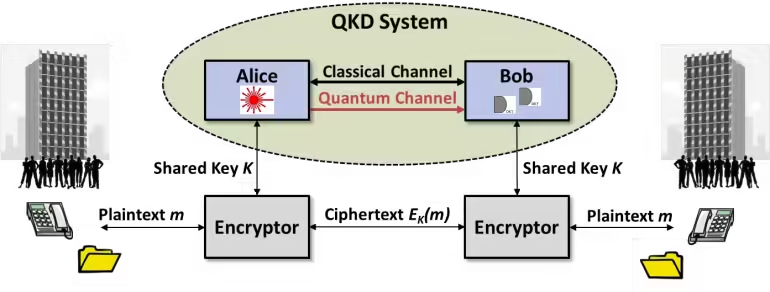
Quantum Key Distribution (QKD): The Security Backbone
Quantum Key Distribution is central to quantum networking security and is primarily used to create and share encryption keys between two parties. The key aspect of QKD that makes it revolutionary is the principle of no-cloning, which states that it is impossible to copy an unknown quantum state. Thus, any attempt to intercept or tamper with a quantum transmission immediately alters the quantum state, alerting the communicating parties to the intrusion.
The most famous QKD protocol is BB84, developed in 1984 by Charles Bennett and Gilles Brassard. In BB84, two users (often named Alice and Bob) share a key by encoding it in the quantum states of photons, which are then transmitted across a quantum channel. If an eavesdropper (referred to as Eve) tries to intercept the communication, they disturb the photons’ states, causing errors that alert Alice and Bob to the intrusion. This tamper-proof approach is why QKD is considered nearly unbreakable.
Traditional Hacking Techniques and Their Limitations
Hacking, as it exists today, employs a variety of techniques that exploit vulnerabilities in traditional network systems. One of the most prevalent methods is phishing, which involves tricking individuals into disclosing sensitive information, such as passwords or credit card numbers, by masquerading as a trustworthy entity through emails or deceptive websites. Despite its effectiveness, phishing attacks rely heavily on human error and can often be mitigated through user education and awareness.
Another widely used approach is the man-in-the-middle (MitM) attack, where the hacker intercepts communications between two parties without their knowledge, allowing the perpetrator to eavesdrop or inject malicious content. Although MitM attacks can be effective in capturing unencrypted data, they are less successful when secure communication protocols, like HTTPS, are implemented. The use of strong end-to-end encryption significantly limits the efficacy of such attacks.
Encryption cracking is also a fundamental technique utilized by hackers to gain unauthorized access to encrypted data. Hackers may employ various methods, such as brute force attacks, to decipher passwords or encryption keys. However, modern encryption algorithms, like Advanced Encryption Standard (AES), provide robust protection due to their complex mathematical structures, making crack attempts considerably time-consuming and resource-intensive.
Despite the sophistication of these traditional hacking techniques, they exhibit inherent limitations, particularly when faced with advancing technology. As networks evolve to incorporate quantum encryption and other innovative security measures, the effectiveness of these conventional methods is diminishing. The very foundation of traditional cyberattacks, which often hinges on exploiting human behavior or system vulnerabilities, may become increasingly irrelevant as organizations adopt cutting-edge security solutions designed to thwart unauthorized access. This suggests a future where traditional hacking methods may struggle to maintain relevance in light of the ongoing advancements in cybersecurity.
Why Quantum Networks Are ‘Unhackable’
Traditional hacking methods rely on vulnerabilities in encryption algorithms or on brute-force computation. However, quantum networks eliminate many of these vulnerabilities by securing communications at the physical level rather than relying solely on complex mathematical encryption. Here’s how quantum networking makes traditional hacking methods ineffective:
- Defense Against Eavesdropping: In a classical network, a hacker can intercept communication without detection. In a quantum network, however, any attempt to intercept the quantum signal changes the quantum states, alerting both parties. This makes eavesdropping nearly impossible.
- Immunity to Brute-Force Attacks: Classical encryption relies on mathematical complexity. Quantum networks, in contrast, use physical properties to ensure security. A brute-force attack would not work against QKD, as the encryption is not based on computational difficulty but on the principles of quantum mechanics.
- Protection Against Quantum Computing Threats: Quantum computers pose a significant threat to classical encryption, as they could theoretically decrypt standard cryptographic algorithms, like RSA, in mere seconds. But since quantum networks don’t rely on these algorithms, they are effectively resistant to quantum computer-based attacks.
Quantum Networking: A Game Changer for Cybersecurity
Quantum networking represents a significant advancement in cybersecurity, fundamentally altering how data is transmitted and secured. The primary advantage lies in its application of quantum mechanics principles, which empower it to address many vulnerabilities inherent in classical networks. Classical network communications often rely on the encryption of data to safeguard against potential breaches, yet issues such as eavesdropping and hacking persist as pressing concerns. Quantum networking, however, utilizes the unique properties of quantum bits, or qubits, to create a more secure framework for data exchange.
One of the critical features of quantum networking is quantum key distribution (QKD). This method employs quantum mechanics to facilitate secure key exchange over potentially compromised channels. QKD ensures that any attempt at interception will immediately alter the state of the transmitted data, alerting parties to the presence of an unauthorized observer. As a result, it provides an unprecedented level of security that traditional encryption methods cannot match. The implications of this technology extend beyond mere data protection; they encompass the very foundations of secure communication.
Additionally, quantum entanglement plays a vital role in enhancing security in quantum networks. When two particles become entangled, the state of one instantly influences the state of the other, no matter the distance separating them. This phenomenon can be harnessed to develop secure communication protocols that are resilient against common hacking techniques. For example, utilizing entangled particles for message transfer can detect any alterations made during transmission, providing immediate feedback about the integrity of the communication channel.
Overall, quantum networking not only addresses existing vulnerabilities but also fortifies the future of cybersecurity against an evolving threat landscape. As organizations increasingly adopt quantum technologies, they are likely to experience a substantial reduction in cyber threats, heralding a new era of information security.
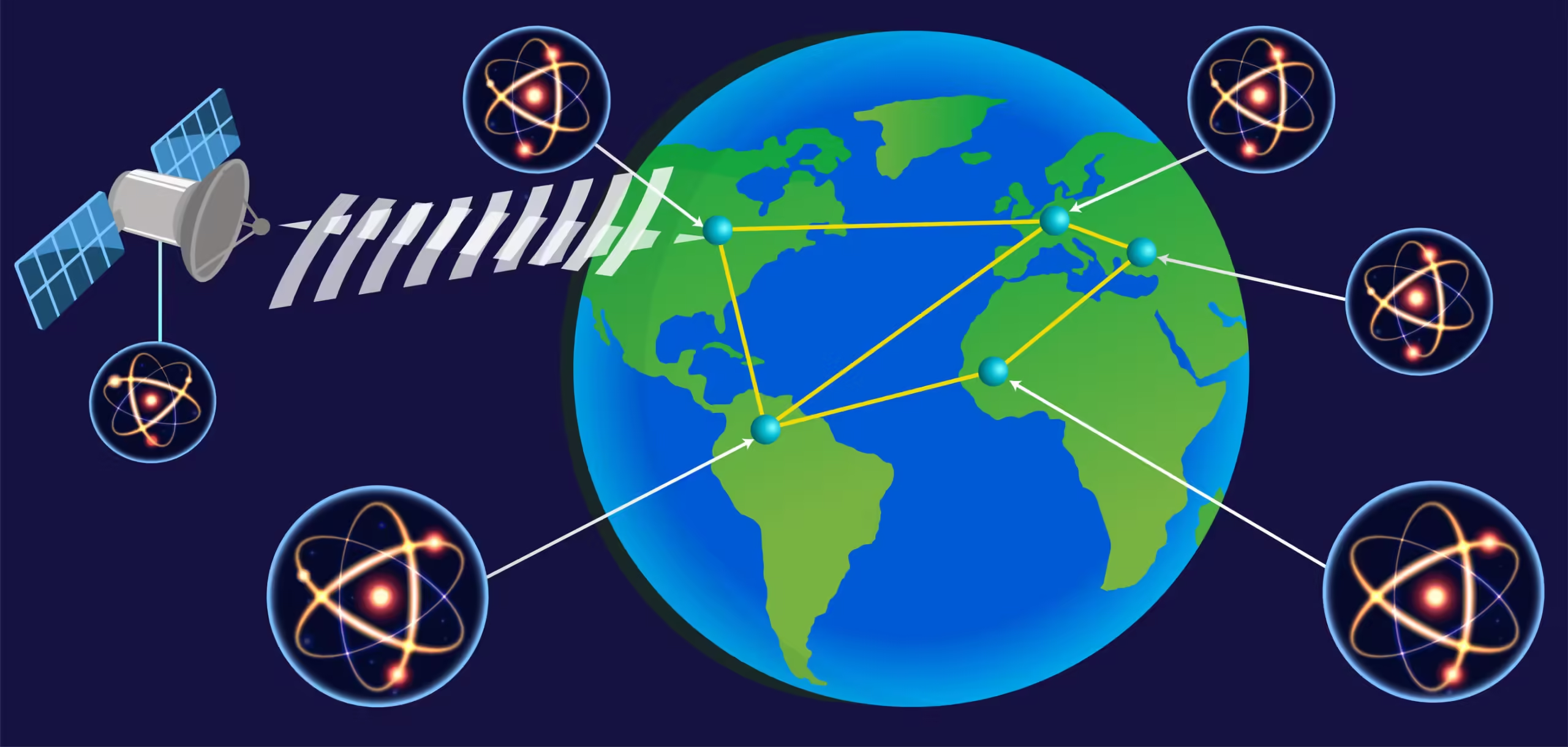
Entanglement and Quantum Repeaters: Extending Quantum Networks
Quantum entanglement allows for “quantum teleportation,” where the state of one qubit can be transferred to another, distant qubit without physical transmission. This is a game-changer for networking, as it allows information to be shared instantaneously over potentially vast distances without traditional data transmission methods.
However, maintaining entanglement over long distances is challenging due to a phenomenon known as quantum decoherence, where quantum states degrade over distance. Quantum repeaters are crucial for addressing this limitation. These devices enable the preservation of entanglement across large distances, extending the reach of quantum networks. They work by entangling pairs of particles in stages, effectively relaying the entangled state without degradation. Quantum repeaters are the key to creating a large-scale quantum internet, capable of secure, long-distance communication.
Comparing Quantum Networking to Classical Networking
Quantum networking represents a significant evolution from classical networking, which has served as the backbone of internet communication for decades. Classical networking relies on bits, which can exist in one of two states: 0 or 1. In contrast, quantum networking utilizes qubits, which can exist in multiple states simultaneously due to the principles of superposition and entanglement. This fundamental difference presents various advantages, primarily in the areas of security, speed, and resilience.
One of the most significant benefits of quantum networking is its inherent security. Classical encryption methods can be vulnerable to sophisticated hacking techniques, as attackers can intercept and manipulate data packets without detection. However, quantum networking employs quantum key distribution (QKD), allowing two parties to share a secret key securely. If an attacker attempts to intercept the qubits, the process disturbs their state, alerting the parties involved of a potential breach. This results in a security framework that is theoretically unbreakable, offering protection that classical systems cannot match.
In terms of data transfer rates, quantum networking showcases remarkable efficiency. Quantum entanglement allows for instant information transfer between qubits, regardless of distance. This capability could potentially eliminate latency issues that plague classical networks, enhancing the speed and responsiveness of data exchanges. High-speed quantum communication can significantly influence various sectors, including finance, healthcare, and telecommunications, where timely information is crucial.
Moreover, quantum networks are designed to be more resilient against external attacks. Classical networks often face disruptions due to cyber threats, such as Distributed Denial of Service (DDoS) attacks. Quantum networking’s unique architecture enables it to effectively withstand these challenges, making it a robust alternative for future communication infrastructure.
Ultimately, the transition from classical to quantum networking signifies not only a technological leap but also a transformative solution that addresses critical challenges facing current communication systems.
Quantum Cryptography: Reinventing Security
Quantum cryptography goes beyond QKD to offer other security measures based on quantum mechanics. For example:
- Quantum Digital Signatures: These allow for the verification of a sender’s identity without the need for a classical cryptographic signature. In a quantum network, digital signatures cannot be forged or tampered with because of the physical properties of qubits.
- Quantum-Safe Algorithms: While not strictly part of quantum networking, quantum-safe algorithms are cryptographic protocols designed to withstand attacks from quantum computers. These algorithms are becoming essential for classical networks as quantum computing advances, ensuring that even classical communications can remain secure in a quantum-dominated world.
Real-World Applications and Impacts on Hacking
Quantum networking’s robust security features make it particularly valuable for industries where data integrity and confidentiality are paramount, such as finance, defense, healthcare, and national infrastructure. Here’s how quantum networks could transform cybersecurity across sectors:
- Financial Sector: Quantum networking could protect banking transactions and financial records, making it impossible for hackers to access sensitive information or disrupt trading activities. Quantum encryption can ensure that customer data and transactions remain confidential and tamper-proof.
- Healthcare: Patient data in healthcare systems is a prime target for hackers. Quantum networks could prevent unauthorized access to medical records, safeguarding patient privacy.
- Military and Government Communications: Secure communication is critical in national defense. Quantum networks could protect sensitive communications, intelligence, and infrastructure systems, making espionage and cyber attacks on governmental systems far more difficult.
Current Developments in Quantum Networking
The field of quantum networking has experienced considerable advancements in recent years, fostering an environment ripe for innovation and research. In particular, scientists have been making strides in quantum communication methods, which utilize principles of quantum mechanics to transmit information securely. One notable breakthrough is the development of quantum repeaters, devices designed to extend the range of quantum communication systems. These repeaters allow for the entanglement of particles over long distances, thus enabling reliable data transfer without the risk of eavesdropping, a significant concern in classical networks.
Research initiatives have begun to focus on creating more robust quantum key distribution (QKD) protocols. These protocols offer a highly secure way to exchange cryptographic keys, ensuring that any interception attempt would be immediately detectable. Recently, studies have demonstrated the use of satellite links for QKD, effectively overcoming geographical limitations and allowing for global secure communications. Such initiatives showcase the potential of quantum networks to support a new era of cybersecurity, given their fundamental resistance to traditional hacking methods.
In addition to academic endeavors, several large-scale projects are currently underway. For instance, the European Union’s Quantum Internet Alliance aims to develop a quantum internet architecture, enhancing the networking capabilities necessary for emerging quantum technologies. Similarly, China has been leading efforts through its Quantum Communication Satellite, Micius, which successfully established secure communication links between multiple locations. These projects not only validate the theoretical principles of quantum networking but also bridge the gap between theory and practical applications.
Overall, the current landscape of quantum networking indicates a positive trajectory toward fully operational quantum systems, with ongoing research and development propelling the field forward. These advancements promise not only to enhance communication security but to fundamentally alter the ways in which we connect and share information in the future.
Challenges and Limitations of Quantum Networking
Quantum networking presents an innovative approach to enhancing cybersecurity; however, it is not without its challenges and limitations. One prominent obstacle is the technical complexity involved in the establishment and maintenance of quantum networks. Quantum entanglement, a core principle of quantum networking, requires precise conditions and sophisticated technology to maintain the integrity of the quantum states over long distances. This inherent fragility of quantum bits, or qubits, makes them susceptible to loss and decoherence, posing significant hurdles in real-world applications.
Additional technical challenges include the need for developing robust quantum repeaters, which are essential for extending the range of quantum communication. Current advancements in this field are promising, but the fabrication and deployment of these devices at scale remain a significant technical burden. The integration of quantum networking with existing classical networks also presents compatibility issues that require careful engineering solutions.
Cost is another critical factor hindering the widespread adoption of quantum networking. The advanced technologies necessary for quantum communication, such as single-photon sources and high-efficiency detectors, entail substantial research and development investments. As a result, creating and deploying quantum networks can be prohibitively expensive for many organizations, particularly small to medium-sized enterprises. This financial barrier needs to be addressed to facilitate broader implementation.
Finally, there is a stark need for more comprehensive infrastructure to support quantum networking. Establishing a network that can accommodate both quantum and classical communications requires significant investment in research, development, and physical infrastructure, such as fiber-optic cables and ground stations. As the technology is still evolving, the current gap in infrastructure makes it challenging to realize the full potential of quantum networking.
The Future of Cybersecurity in a Quantum World
The advent of quantum networking is poised to revolutionize the landscape of cybersecurity, presenting both unprecedented advantages and significant challenges. As quantum technologies mature, organizations must adapt to a new paradigm of cybersecurity that hinges on the principles of quantum mechanics, such as superposition and entanglement. These principles enable the development of techniques like quantum key distribution (QKD), which offers a level of security unattainable in classical cryptographic systems. With this development, the ability to secure communications against eavesdropping becomes more effective, offering potentially unbreakable encryption.
The implications for businesses are profound. Organizations will need to invest in quantum-safe encryption methods and integrate these into their existing cybersecurity frameworks. As cyber threats continue to evolve, the emergence of quantum computing could lead to more complex attack vectors; however, the tools developed within the quantum realm may also provide solutions to counteract these threats. The shift towards quantum networking could catalyze a new era of collaboration between industries, enhanced global regulatory frameworks, and a focus on advancing quantum cybersecurity measures.
For individuals, the proliferation of quantum technologies raises concerns regarding data privacy and security. It is critical for consumers to be aware of the potential risks associated with quantum hacking. With the prospect of powerful quantum computers being utilized for malicious purposes, awareness and education on personal cybersecurity practices will become imperative. Society at large will need to navigate the complexities of quantum ethics, the implications of state-sponsored quantum hacking, and the fair use of these emerging technologies.
In conclusion, the future of cybersecurity in a quantum world appears to be a double-edged sword. While quantum technologies promise enhanced security measures, they also introduce a new landscape of challenges that must be managed diligently. As the quantum era unfolds, ongoing education, investment, and collaboration will be essential to safeguard against the threats of tomorrow while capitalizing on the opportunities presented by this transformative technology.
The Road to Unhackable Networks
Quantum networking represents a leap forward in securing data and communications. By relying on the principles of quantum mechanics rather than computational security, quantum networks promise to end the era of conventional hacking and usher in a new age of data protection. Although still in the developmental stages, ongoing advancements in quantum networking and quantum cryptography hold the promise of rendering many current cybersecurity concerns obsolete.
In the coming years, as more industries adopt quantum networking, hacking as we know it could truly become a thing of the past. However, reaching this goal will require overcoming significant technical and financial barriers, alongside continued research and innovation in the field.