In today’s digital-first business world, data is currency—and just like any valuable asset, it needs to be protected not only from external hackers but also from unintentional or malicious internal access.
One of the most practical and effective ways to limit internal risk is by implementing Role-Based Access Control (RBAC).
If you’ve heard about RBAC but aren’t quite sure how to implement it step by step, this guide is for you. Based on real-world experience and IT governance practices, let’s walk through how to build an RBAC system that works.
What is Role-Based Access Control (RBAC)?
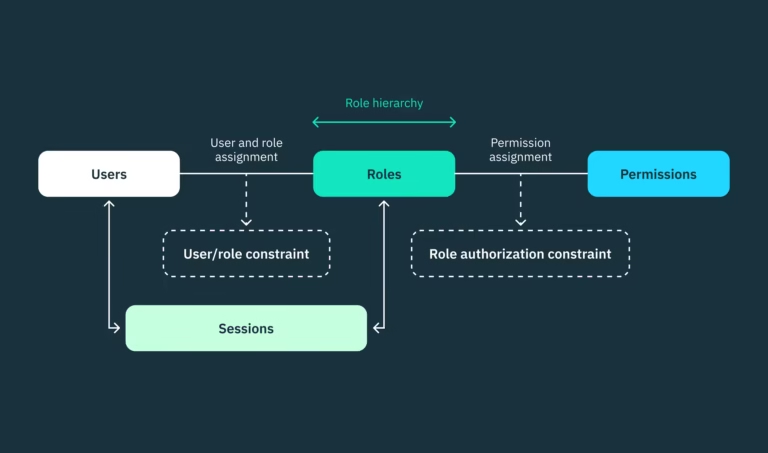
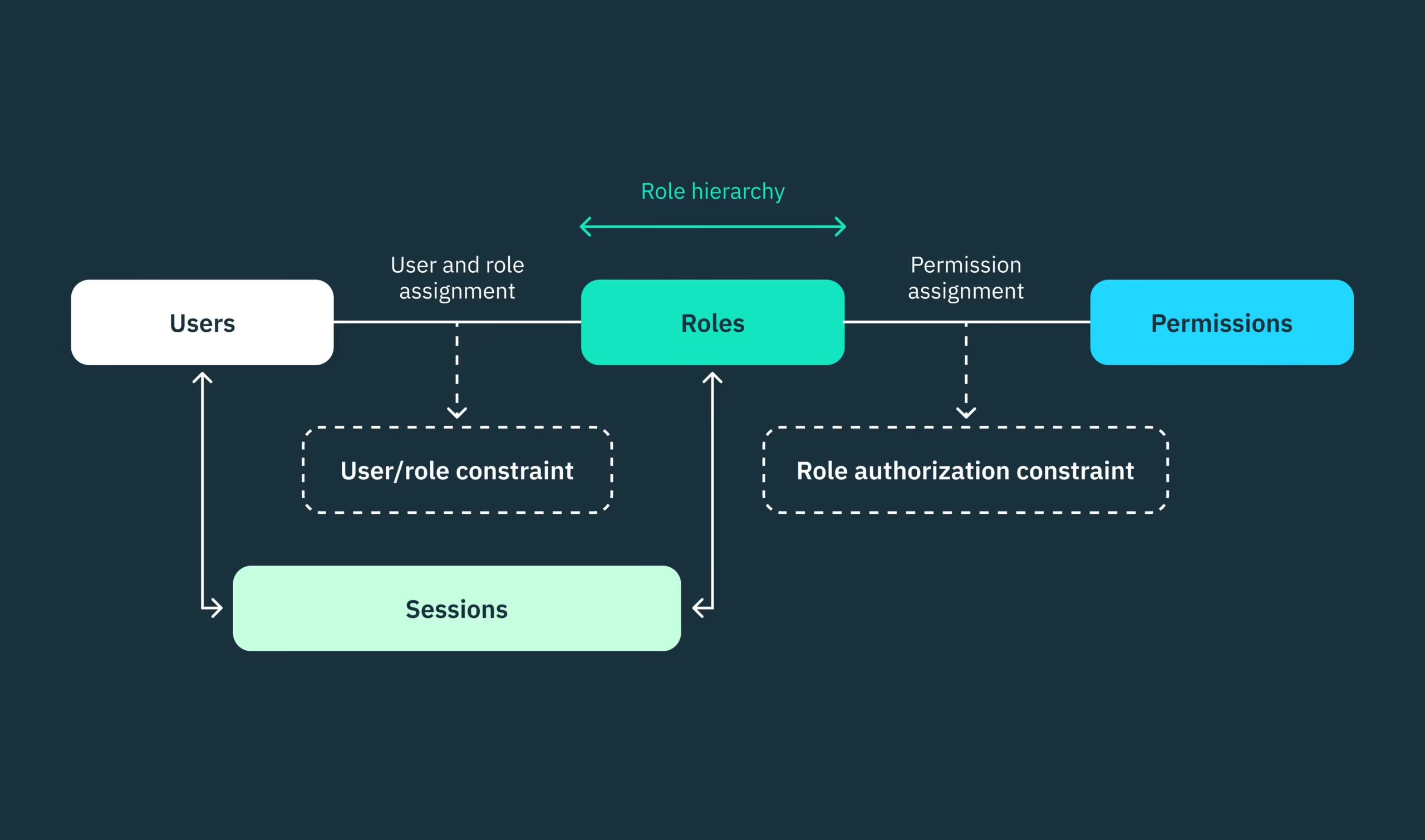
RBAC is a method of restricting system access based on a user’s role within an organization. Instead of assigning permissions to each user individually, you assign permissions to roles (like HR Manager, Developer, Finance Analyst), and then assign users to those roles.
This ensures:
- Least-privilege access (users only see what they need)
- Better compliance and audit control
- Reduced internal data leak risk
🧩 Step-by-Step Guide to Setting Up RBAC
🔍 Step 1: Understand Your Business Functions and Data Sensitivity
Start by mapping out your organization. Identify:
- What departments exist (HR, IT, Finance, Sales, Administration etc.)
- What systems and data each department accesses
- Which data is sensitive, confidential, or regulated (e.g., customer PII, payroll data, source code)
💡 Tip: Sit with team leads to understand day-to-day tasks and tools they use. This avoids over- or under-provisioning access later.
🗂️ Step 2: Define Roles Clearly
Now that you know what functions exist, define roles based on real job responsibilities, not just job titles.
For example:
- Sales Executive – Needs access to CRM, lead data
- HR Manager – Needs access to employee records, not financials
- DevOps Engineer – Needs access to production environment logs, not payroll data
🚫 Avoid creating roles like “Super Admin” for convenience. This often leads to excessive access.
🛠️ Step 3: Group Permissions by Role
Once roles are defined, list the exact permissions each role needs.
Example for a Finance Analyst:
- Read access to financial reports
- Write access to budget planning sheets
- No access to HR or source code repositories
💡 Use spreadsheets or an IAM (Identity and Access Management) tool to track this mapping.
👥 Step 4: Assign Users to Roles
Now, assign each employee to the appropriate role(s). This should be done through an IAM system like:
- Microsoft Active Directory
- AWS IAM
- Okta
- Google Workspace Admin Console
Avoid assigning access directly to users unless absolutely necessary. Stick to role-based assignment.
🔁 Step 5: Implement and Test
Roll out RBAC gradually, preferably department by department.
Things to test:
- Can users perform their normal tasks?
- Are they blocked from accessing data they shouldn’t see?
- Is there any business disruption?
🧪 Tip: Use test accounts or shadow users to simulate access scenarios.
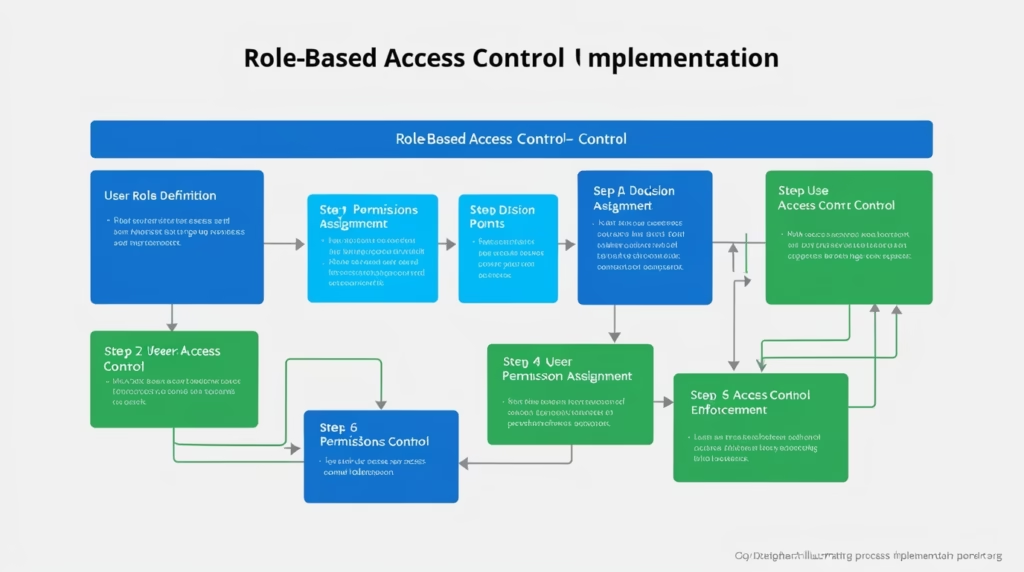
🧹 Step 6: Clean Up Legacy Access
Most organizations have “access bloat”—users with permissions they no longer need.
Once RBAC is in place:
- Audit existing permissions
- Remove direct access not tied to roles
- Document changes
📌 Tools like Azure Access Reviews or AWS IAM Access Analyzer can help.
🔄 Step 7: Review Roles Regularly
Business roles evolve. New tools are introduced. Employees move between teams.
Schedule quarterly or biannual reviews to:
- Reassess if roles are still valid
- Update permissions
- Remove inactive users
🧩 Combine this with your offboarding checklist to remove access immediately when someone leaves.
🛡️ Final Thoughts
RBAC is not just a technical task—it’s a collaboration between IT, HR, department heads, and compliance. When implemented right, it dramatically reduces the risk of accidental data exposure, insider threats, and non-compliance issues.
Start small, stay consistent, and make sure documentation is up to date.
If your organization isn’t using RBAC yet, the best time to start is today.
Have you implemented RBAC in your organization? What challenges did you face?
Share your thoughts or questions in the comments!